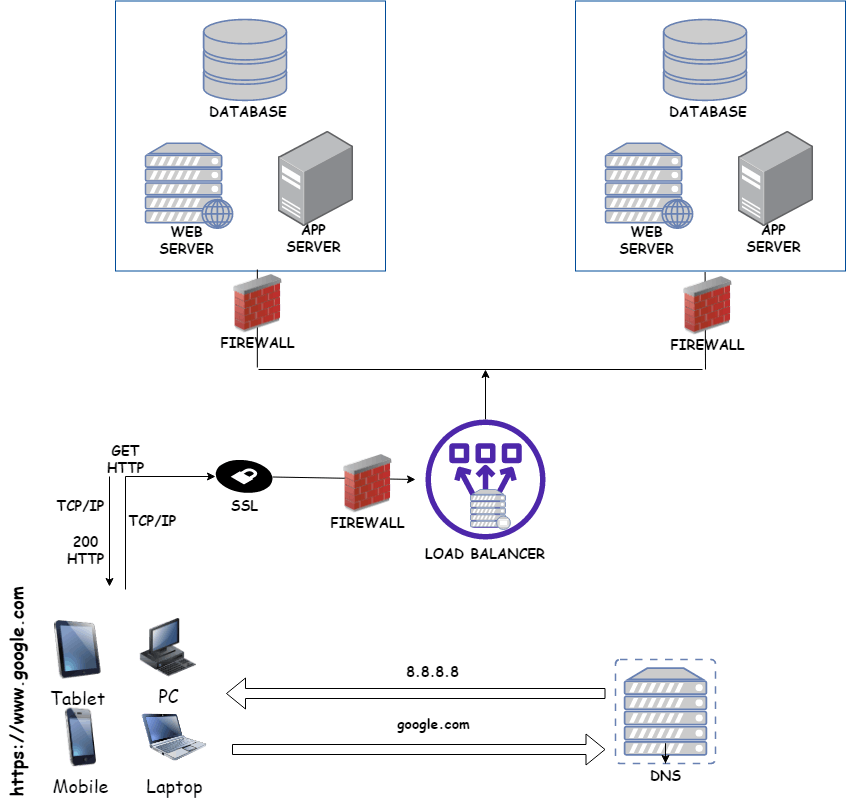
What Happens When You Type Google.com in Your Browser and Press Enter
Network and Web Infrastructure Components
In two shakes of a lamb tale, you got a response and that feels good. But have you ever wondered what goes on behind the scenes when you open up your browser, type https://www.google.com into the address bar, and hit enter? What happens next? How does your computer know where to find Google, and how does it display the website on your screen? Let’s take a journey through the various systems and technologies involved in this process.
First up is the DNS (Domain Name Server) request. When you hit enter, your computer sends out a DNS request to translate the human-readable domain name www.google.com into an IP (Internet Protocol) address that computers can understand. This request is sent to a DNS server, which responds with the IP address of the server hosting Google’s website.
With the IP address in hand, your computer establishes a connection to Google’s server using the TCP/IP protocol. TCP (Transmission Control Protocol) is responsible for breaking down the data into packets and ensuring that the information you’re sending and receiving is intact and error-free. IP (Internet Protocol) handles the addressing and routing of the packets across the internet.
Before the connection is fully established, your computer's firewall steps in to check whether the IP address is safe to connect with. The firewall is like a gatekeeper that blocks any potentially harmful traffic from entering your computer. If the IP address is safe, the firewall allows the connection to proceed.
Once the connection is established, your browser and Google’s server negotiate an SSL (Secure Sockets Layer) handshake. SSL is a protocol that encrypts the data being sent between your computer and the server, protecting it from being intercepted and read by unauthorized parties. During the SSL handshake, your browser verifies that Google’s SSL certificate is valid and has not been tampered with. This certificate contains information about the website’s identity and the encryption keys used to establish the secure connection.
Now that the connection is secure, the request is passed on to a load balancer. Load balancers are responsible for distributing the traffic across multiple servers to ensure that no single server is overloaded. The load balancer picks a server and forwards the request to it.
The server that receives your request is known as the web server. The web server retrieves the HTML, CSS, and JavaScript files that make up the website and sends them back to your browser. Your browser then processes these files to display the website on your screen.
But what if the website has dynamic content, like search results or personalized recommendations? In that case, the web server may need to interact with an application server. The application server processes the request and generates the appropriate content. The application server then sends the data back to the web server, which sends it to your browser for display.
Finally, the web server may need to retrieve data from a database to complete your request. This database contains all the information needed to generate the dynamic content you’re looking for. The web server sends a query to the database, which returns the requested data. The web server then sends the data to your browser for display.
And just like that, your Google search is complete. The entire process happens in a matter of seconds, but behind the scenes, there’s a complex system of technologies working together to make it all possible.
CAPTIVATING STORIES THAT DECODE NETWORK AND WEB INFRASTRUCTURE COMPONENTS:
DNS request
TCP/IP
Firewall
HTTPS/SSL
Load-balancer
Web server
Application server
Database
DNS Request
Imagine you're planning a road trip to a new city, and you need directions to get there. You've heard that there's an amazing restaurant you want to try, and you're eager to explore all the sights and sounds of this vibrant metropolis.
But there's one problem – you don't know how to get there. You've heard the name of the city, but you don't have the exact address. What do you do?
You decide to ask for help, and you pull over to the nearest gas station. Inside, you see a friendly attendant who's happy to help you out. You explain your dilemma, and the attendant asks you for the name of the city you're trying to reach.
"Ah, I know just the place," the attendant says. "But you'll need to know the exact address before you can get there."
The attendant pulls out a phone book and starts flipping through the pages, looking for the address you need. After a few minutes, the attendant finds what you're looking for and jots it down on a piece of paper.
"Here you go," the attendant says. "That's the address you need to get to your destination."
In the world of the internet, the process of finding the address of a website is similar to asking for directions at a gas station. When you enter a website address like "www.google.com" into your browser, your computer doesn't know where to find it.
That's where the DNS (Domain Name System) comes in. DNS is like a giant phone book for the internet, and it contains the addresses of all the websites on the web. When your browser sends a DNS request, it's asking for the address of the website you want to visit.
Just like the gas station attendant, the DNS server looks up the address of the website in its database and returns it to your computer. Your browser then uses that address to connect to the website's server and retrieve the information you're looking for.
TCP/IP
Imagine you're trying to have a phone conversation with a friend who lives in a different country. You pick up the phone and dial their number, but as soon as they answer, you can't hear them properly. There's too much static and interference, and the connection keeps cutting out.
You realize that the problem isn't with your friend's phone, but with the fact that you're trying to communicate over a long distance. The signal has to travel through multiple phone lines, satellites, and routers before it reaches your friend, and each step of the way, there's a risk of interference or signal loss.
In the world of the internet, the same problem exists when you try to connect to a website. Your computer has to send a signal across the internet to the server hosting the website, and just like a phone call, there's a risk of interference or signal loss along the way.
That's where TCP/IP comes in. TCP/IP stands for Transmission Control Protocol/Internet Protocol, and it's a set of rules and protocols that govern the way information is sent and received over the Internet.
When your browser sends a request to a website, it uses TCP/IP to break the information into small packets, like letters in an envelope. Each packet is labeled with information about its destination and content, and it's sent out into the vast network of routers and servers that make up the internet.
As each packet travels across the internet, it's checked for errors and reassembled at its destination. If any packets are lost or corrupted along the way, TCP/IP ensures that they're resent until the entire message is complete and error-free.
In other words, TCP/IP is like a skilled translator and courier, making sure that your messages are delivered accurately and reliably across the vast, chaotic landscape of the internet.
Firewall
Think of a firewall as a security guard that stands between your computer and the internet, keeping an eye out for any suspicious activity and making sure that only authorized information is allowed through.
When you type in a website address and hit "Enter" in your browser, the request is sent out across the internet. But before the website's server can send back the requested data, it has to get through your computer's firewall.
The firewall checks the incoming data to make sure that it's coming from a trusted source and that it doesn't contain any malicious code or viruses. If everything checks out, the firewall allows the data to pass through and reach your computer.
But if the firewall detects something suspicious, like a virus or a phishing attempt, it blocks the data from coming through and alerts you to the potential threat. This gives you the chance to take action to protect your computer and your personal information.
In other words, a firewall is like a vigilant security guard that keeps watch over your computer and makes sure that only the right people and information are allowed through. It's an essential component of any computer's security system, helping to keep you safe and secure while you browse the internet.
HTTPS/SSL
Imagine you're sending a secret message to a friend, but you don't want anyone else to be able to read it. You could write the message in code, but anyone who knows the code could still read it. Instead, you decide to use a special lockbox that only you and your friend have the key to. You put the message in the lockbox, lock it up, and send it to your friend. When they receive it, they use their key to unlock the box and read the message.
That's essentially what HTTPS/SSL does for your online communication. When you connect to a website that uses HTTPS/SSL, your computer and the website's server exchange keys to create a secure, encrypted connection. This means that any information you send to the website, such as your login credentials or credit card information, is locked up and protected from anyone who might try to intercept it.
Just like the lockbox in our story, the encryption used by HTTPS/SSL is nearly impossible to crack without the right key. This means that even if someone does manage to intercept your data, they won't be able to read it without the key.
So the next time you see that little lock icon in your browser's address bar, remember that HTTPS/SSL is working behind the scenes to keep your personal information and data safe from prying eyes. It's like a secret lockbox that only you and the website's server have the key to, making sure that your online communication is secure and protected.
Load Balancer
Think of it like a queue of people waiting to enter a building. If only one door is open, people will have to wait longer to enter, and the door operator may become overwhelmed. However, if there are multiple doors open, people can enter more quickly and the door operators can handle the influx of people more easily.
Similarly, a load balancer distributes incoming network traffic across multiple servers, allowing the servers to work together to handle requests and prevent any single server from becoming overloaded. This improves performance, reduces the risk of downtime, and allows the system to scale more easily to handle increased traffic.
In addition to balancing traffic across servers, load balancers can also perform other functions, such as caching frequently accessed data and encrypting traffic to improve security.
Web Server
A web server is a software program that runs on a computer or a network of computers and is responsible for serving web content to clients, such as web browsers. It is like a digital concierge that directs clients to the right web content and ensures that they receive the content they need in a timely and efficient manner.
To understand this better, think of a web server as a virtual tour guide. Just like a tour guide, a web server helps visitors navigate through a large and complex environment, in this case, the Internet. It listens to incoming requests from clients, checks what content is being requested, and serves up the appropriate content, just like a tour guide who directs visitors to different attractions based on their interests.
The web server can also process web applications, handle database access, and enforce security protocols, just like a tour guide who provides additional information and context to visitors, takes them on a guided tour of a museum or a city, and ensures their safety and security during the tour.
Application Server
An application server is like the conductor of an orchestra. It is a software platform that sits between the web server and the database and is responsible for managing and coordinating the various components of an application.
Imagine you are listening to an orchestra, with different musicians playing different instruments. Each musician plays their part, but they need someone to coordinate and synchronize their performance. This is the role of the conductor, who sets the tempo, cues the musicians, and ensures that the music flows smoothly.
Similarly, an application server is like a conductor that manages the flow of data between the web server and the database and coordinates the different components of an application. It provides a framework for developing and deploying applications and handles tasks such as load balancing, session management, caching, and security.
The application server can also process business logic and transactional data, just like a conductor who interprets the musical score and ensures that the music is played according to the composer's intentions.
Finally, an application server can be configured to handle a high volume of traffic and scale up or down as needed, just like a conductor who can adjust the tempo and dynamics of the music to match the size and energy of the audience.
Database
Imagine you are the owner of a large toy store that sells a wide range of toys to children of all ages. To keep track of all the toys in the store, you use a computer system that stores information about each toy such as its name, price, manufacturer, and the number of units in stock. This computer system is like a database that helps you manage your inventory.
A database is a structured collection of data that is stored and organized in a way that makes it easy to retrieve and manage information. It's like a digital filing cabinet that stores information in an organized and logical manner, making it easy to search, sort, and filter the data.
In the case of the toy store, the database helps you keep track of inventory levels, sales, and other important information that is crucial for running a successful business. For example, you can use the database to generate reports on which toys are selling well and which ones are not, making it easier to make informed decisions about what products to stock in the future.
Databases are used in many industries, from healthcare to finance to e-commerce. They help businesses and organizations store and manage large amounts of data efficiently, which is essential in today's data-driven world.
In summary, when you type https://www.google.com into your browser and press enter, a complex sequence of events is initiated. First, a DNS request is sent to translate the domain name into an IP address. Then, TCP/IP protocols are used to establish a connection with the server. A firewall verifies the connection and HTTPS/SSL protocols are used to encrypt the data being transmitted. A load-balancer distributes the requests to multiple web servers, which process and serve the request using application servers and databases. As a software engineer, having a deep understanding of these technologies is crucial in building fast, secure, and reliable applications. Businesses with websites need to understand these technologies to ensure their websites are optimized for speed, security, and reliability, and to innovate and create unique and engaging web experiences.

